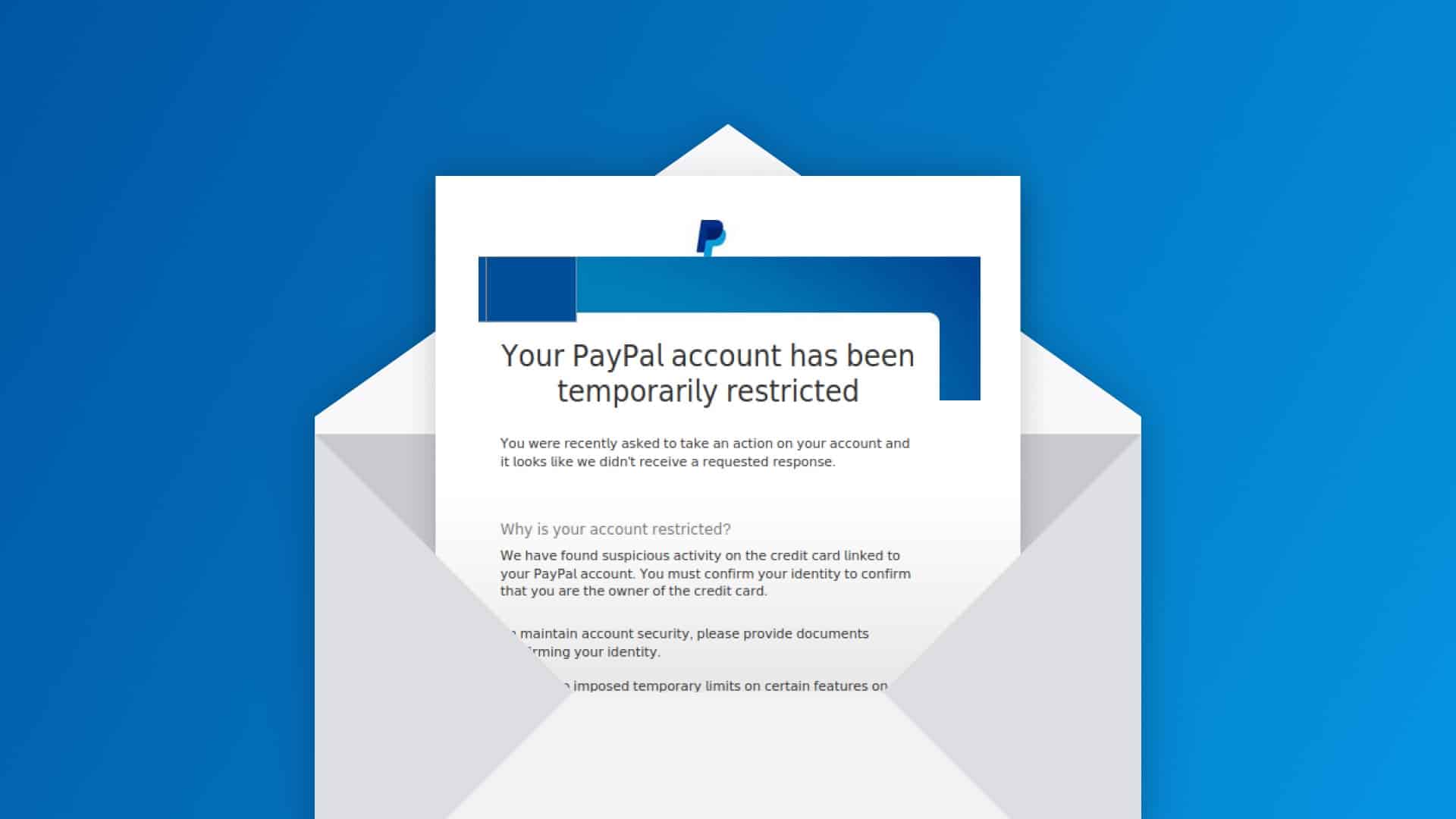
This week, Tessian’s threat intelligence researchers detected a relatively sophisticated phishing attempt impersonating PayPal, the global payment services provider. The threat actor sent an email requesting action from the victim, prompting them to click on the login button, leading to a malicious website.
Social engineering-based cyber attacks like this, usually leveraging a form of phishing via email, have become a common phenomenon both at work and in our personal lives. Threat actors are able to perpetrate these attacks through a range of techniques, leveraging information gathered by random coincidence or through open source intelligence (OSINT) tactics.
In fact 70-90% of all successful breaches are attributed to social engineering, with 96% of all phishing attacks delivered via email. This is why advanced phishing attacks are seen as a growing cybersecurity challenge.
All it takes is one click
Phishing attempts are used for a range of cybercriminal objectives, for example delivering malware including ransomware onto unsuspecting victims’ computers. Often phishing campaigns are also waged for the harvesting of credentials to execute an account takeover (ATO) attack.
They’re difficult to spot, too. Phishing attempts can appear to be very legitimate, even to the trained eye.
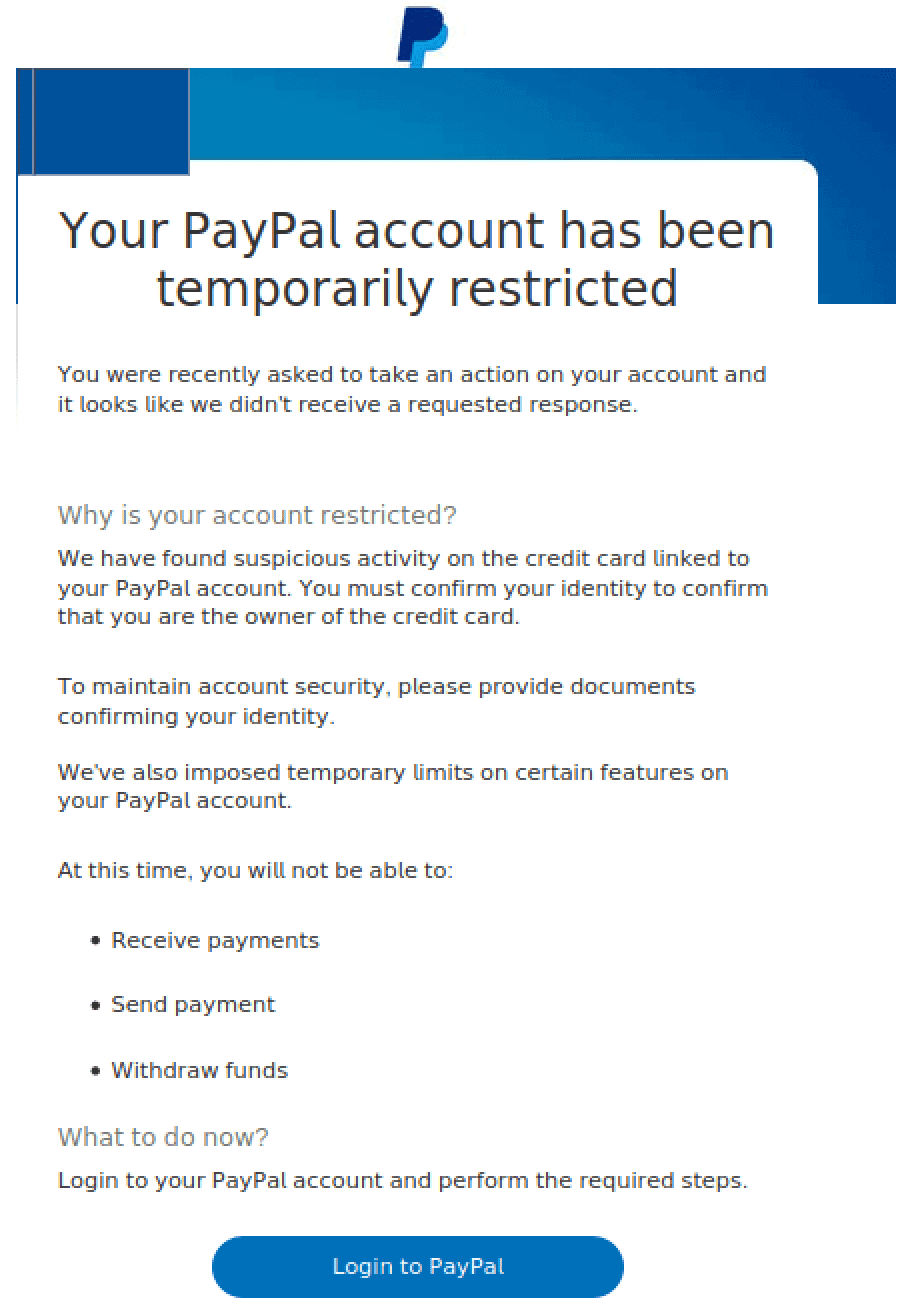
The phishing attempt targeted PayPal customers, and used common phishing tactics, including leveraging corporate logos hosted via a third-party service provider, and creating a sense of urgency by stating that “Your PayPal Account Has Been Temporarily Restricted”.
But, when you actually click “Login to PayPal” as instructed, you’re directed to
hxxps://me2[.]do/xZD4rPKB
Which redirects to
hxxps://docs[.]05fmxoujyghzb[.]club/tmp/index/wildtt.php?97giuywdae
Despite the unusual URL, the landing page looks legitimate, and will prompt users to enter their login details. This information is then captured by cybercriminals in a scheme known as credential harvesting.
Just as every effort was taken to make the webpage look legitimate, every effort was also taken to mimic the authenticity of a legitimate PayPal customer email, including:
Email Images
The email source points to linkpicture[.]com domain, a used free image hosting service. The primary reason for using a free service like this? It enables the threat actor to avoid any tie-backs to personal infrastructure, which enables a relatively high degree of anonymity and separation for carrying out the attack.

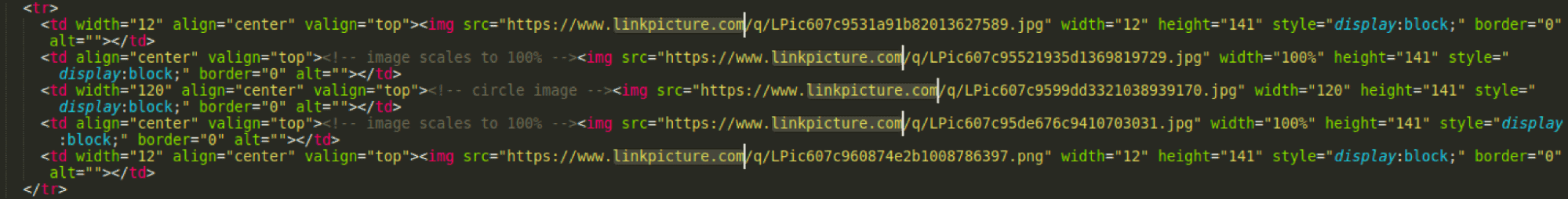
Quoted Printable Encoding
The threat actor also used quoted printable encoding inside key email fields and sections of the HTML body of the email – a common tactic for obfuscating spam filters. Web browsers automatically decode this encoded text to readable text displayed to the end user.
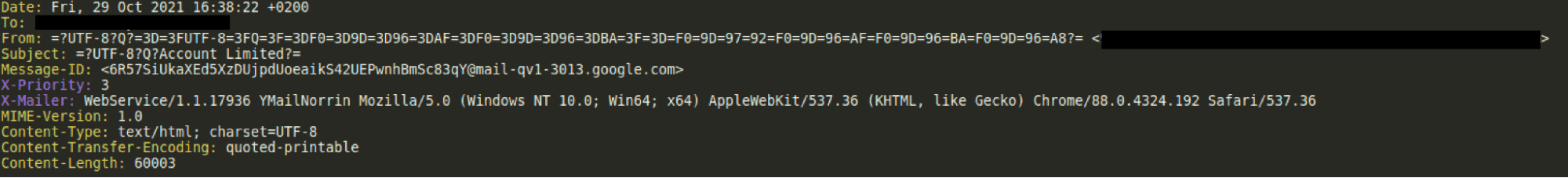
Display Name Decoded
When adding the display name the attacker attempted to double encode part of it but this didn’t work which is why the first string does not fully decode.
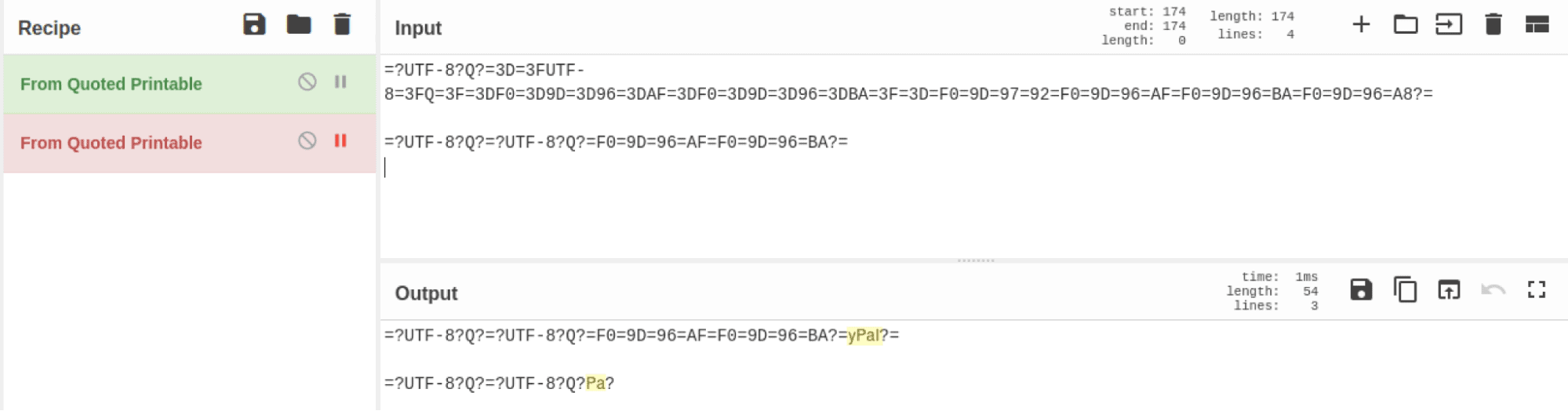
Body – Email Headline
Code snippet from the email HTML body showing the headline encoded using quoted printable

Email Headline Decoded

Enhancing “authenticity”
Impersonating well-known and trusted brands like PayPal is a common modus operandi for phishing attacks. According to Tessian research and the analysis of 2 million malicious emails, Microsoft, Amazon, and Zoom all ranked among the top most impersonated brands. Likewise, the financial services sector tends to be heavily targeted in phishing attacks.
The threat actor also used what appears to be legitimate footer links from PayPal to enhance the appearance of authenticity of the phishing email – another common tactic observed in phishing attempts. The links included however are empty and have no URL included.

Additional observations of interest, and avenues for further research
The HTML body contains the name of a UK based retailer “Sainsbury’s” indicating the reuse of this template for likely earlier phishing attempts, targeting a different retailer’s customers. The threat actor has, in this instance, forgotten to update the information. There might be utility in purchasing similar phishing templates off the dark web to identify phishing attack trends and indicators.
It also pays dividends for organizations to stay aware of how email security threats are evolving, with threat actors continuously adapting social engineering methods to bypass legacy, rule-based email security controls. Educating employees about threats and how to spot them is important, too.
What to do if an email if you think an email is suspicious
Now that we’ve examined this particular example, we need to address what you should do if you suspect you’re being targeted by a phishing attack.
- If anything seems unusual, do not follow or click links or download attachments.
- If the email appears to be from a government organization or another trusted institution, visit their website via Google or your preferred search engine, find a support number, and ask them to confirm whether the communication is valid.
- If the email appears to come from someone you know and trust, like a colleague, reach out to the individual directly by phone, Slack, or a separate email thread. Rest assured, it’s better to confirm and proceed confidently than the alternative.
- Contact your line manager and/or IT team immediately and report the email.